The workplace identity landscape has fundamentally shifted. Threat actors have abandoned traditional hacking in favor of something far more effective: impersonating legitimate users through AI-powered social engineering and synthetic identity creation.
The result? 80% of breaches now stem from system intrusion attack patterns, with 79% using malware-free tactics that perfectly mimic legitimate user behavior. The average breach has hit $4.4 million—a 10% increase year-over-year.
Most security frameworks still operate on a dangerous assumption: that possession equals identity. If someone has the password, token, or device they must be legitimate. This thinking creates vulnerabilities that today’s threat actors systematically exploit.
Instead of asking “Do you have the right credentials?” or “Is this a trusted device?” enterprises need to ask “Are you actually you?”
This guide delivers a practical framework for implementing an identity verification solution that stops impersonation attacks while streamlining legitimate access—from mapping your critical vulnerabilities to evaluating identity software vendors that offer seamless integrations with leading IAM platforms and enterprise systems, and provide robust identity verification capabilities.
Start with Your Critical Vulnerabilities
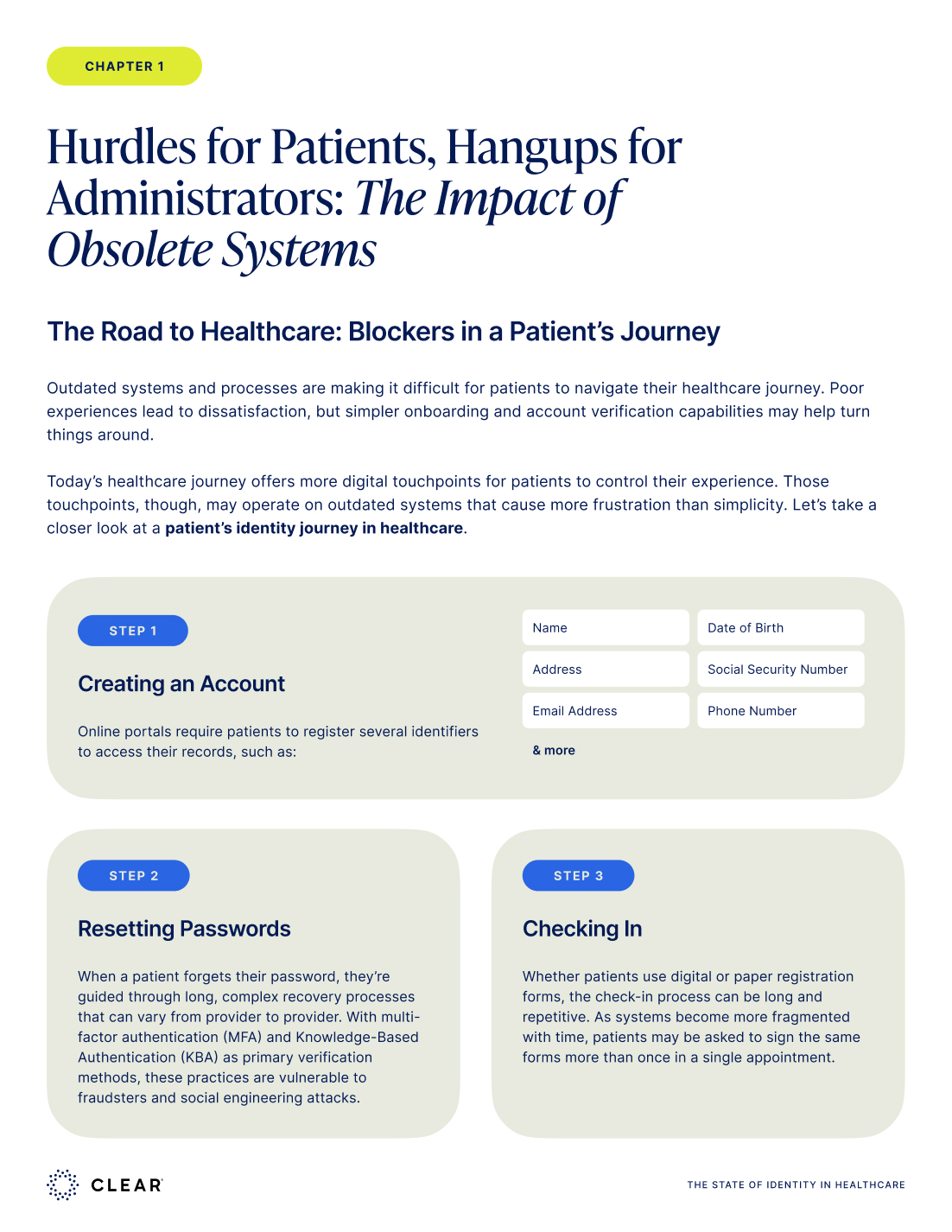
Before selecting an identity software solution, map where breaches actually happen in your organization. This exercise reveals a critical gap: most enterprises focus on technical vulnerabilities while missing the human attack vectors that sophisticated actors prefer.
Map Your High-Risk Points
These four vulnerabilities represent the most urgent threats, but comprehensive workforce identity protection extends across your entire employee lifecycle—from applicant verification and privileged access to help desk authentication and account recovery.
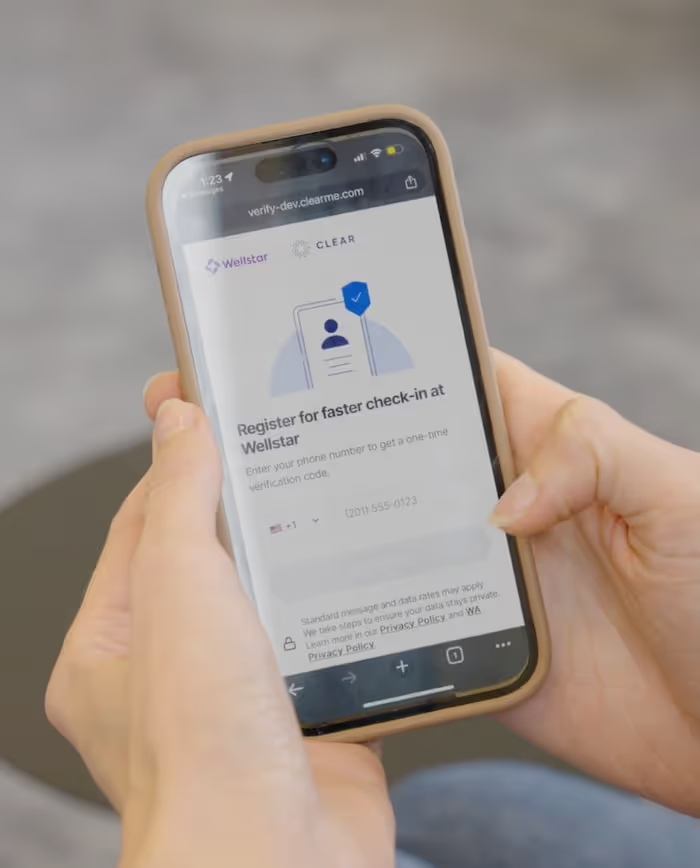
Account creation: A new employee is hired and needs to be onboarded into your system.
Common attack methods:
- Synthetic identity creation using stolen data
- AI-generated credentials that pass basic checks
Account recovery: An employee needs to regain access to an account or reset a password.
Common attack methods:
- Password reset exploitation through social engineering
- Security question manipulation
- Recovery process bypass through impersonation
Privileged access: An employee needs to be given permission to access sensitive or confidential information.
Common attack methods:
- Executive impersonation through social engineering attacks
- Admin rights misuse after credential theft
- Lateral movement through connected systems
Third-party access: External vendors, contractors and partners require systems access to deliver services, creating extended attack surfaces that fraudsters can exploit through social engineering. 47% of workplace breaches occurred through third-party access.
Common attack methods:
- Vendor credential exploitation
- Supply chain identity attacks
- Contractor access exploitation
Calculate the Hidden Costs of Weak Identity Verification
The numbers tell the story:
- Average cost per password reset call: $70+ per interaction
- Average number of password resets per organization annually: 923
That adds up to nearly $65,000 every year spent on password resets alone—and that doesn’t include lost productivity or security risks.
Quick assessment: If your spend on password resets and account recovery is climbing into six figures, your current identity infrastructure is failing on both security and operations efficiency.

Define Your Non-Negotiable Requirements
Resist the urge to jump into vendor demos without clear requirements. Some identity software solutions are just yesterday's authentication wrapped in modern UI. The difference between checkbox compliance and actual security lies in defining exactly what verification means in the age of AI-generated faces and synthetic identities.
Security Standards Your Solution Must Deliver
Multi-layered identity verification:
- Biometric capabilities with PAD-2 certified liveness detection: Prevents identity spoofing and AI-powered impersonation attempts by confirming physical presence and blocking deepfakes, presentation attacks, and virtual webcam injections
- Document authority validation against government-issued IDs: Prevents credential forgery and manipulation by examining security features, holograms, microprinting, and formatting details to detect counterfeit or altered documents
- Source corroboration with authoritative databases: Prevents synthetic identities and sophisticated impersonation by cross-checking personal information against both issuing authorities and trusted third-party data sources
- Device security analysis across 300+ behavioral signals: Prevents account takeovers through compromised device detection by evaluating device reputation, IP behavior, login velocity, and geolocation patterns to identify suspicious activities
- Watchlist screening for compliance requirements: Prevents high-risk transactions with prohibited parties by screening against OFAC sanctions lists, identifying politically exposed persons (PEPs), and detecting negative media associations
This multi-layered approach creates strategic redundancy where even if attackers bypass one verification method, other layers maintain protection and eliminate single points of failure that criminals systematically exploit.
Compliance certifications:
- Identity Assurance Level 2 (IAL2) for high-confidence verification
- Authentication Assurance Level 2 (AAL2) for secure access
- HIPAA compliance for healthcare environments
- SOC 2 Type II certification for enterprise deployment
Adaptive security features:
- Risk-based authentication that can be adjusted to context
- Real-time fraud detection and prevention
Beyond Implementation: Enterprise-Grade Support
CLEAR1 delivers comprehensive support that extends far beyond basic technical integration:
- Fraud Investigation: Submit verification results for triage by CLEAR's in-house security experts, including investigation protocols and escalation procedures for suspected fraud incidents
- Dedicated Technical Resources: Solutions Engineers help manage integration, configuration, and ongoing backend support, while Success Managers lead rollout planning, track performance KPIs, and drive continuous optimization
- Comprehensive Training Programs: Customized team training, live end-user support, and tailored employee communications ensure smooth adoption across your organization
This level of support transforms identity verification from a technical implementation challenge into a strategic security advantage with measurable business outcomes.
IAM Integration Requirements for Seamless Deployment
Confirm these technical capabilities before any demo:
Must-have integrations:
- Native support for leading IAM platforms like Okta, Ping Identity, and Microsoft Entra
- API-first architecture for custom workflows
- Additional enterprise integrations through orchestration partners
- Implementation timeline of days, not months
Operational requirements:
- Minimized IT oversight through turnkey integrations for integration/deployment
- Reusable identity components across applications
- Unified verification policies across multiple applications
- Scalable technology stack
User Experience Standards that Drive Adoption
Set these benchmarks for workforce acceptance:
- 95%+ completion rates for workforce use cases
- User-friendly design (as simple as the snap of a selfie)
- Reusable identity (verify once, use everywhere)
- Average verification for returning users time under 30 seconds
Build Your Evaluation Framework
Evaluate identity software through three critical lenses that determine success or failure in production environments.
Pillar 1: Technical Fit
Rate how well it integrates with your current infrastructure
Ask vendors to demonstrate:
- Integration with your existing IAM with minimal custom development
- Deployment timeline under 30 days for pilot programs
- Scalability to support your user volume, growth projections and ability to support new use cases
- API flexibility for unique workflow requirements
- Enterprise-grade security and reliability standards
Pillar 2: Security Depth and Effectiveness
Test whether it actually verifies humans, not just the device
Require vendors to prove:
- Adaptive authentication that adjusts to risk levels by use case
- Configurable assurance levels for different applications
- Fraud prevention with proven reduction rates (target: 50% minimum)
- Multi-layered approach beyond passwords and basic MFA
Pillar 3: Business Impact
Calculate ROI using this formula: (breach prevention + operational savings) / implementation cost
Demand concrete case studies like the following example.
Real-world example: Tampa General Hospital strengthened account recovery security and achieved:
- 80% of account recovery requests automated through secure self-service capabilities
- 99% faster resolution for help desk calls (MFA reset time cut from 4.5 days to 20 minutes)
- 22% reduction in all account-related support calls
- Eliminated social engineering vulnerabilities in password reset workflows
The Competitive Advantage of Modern Identity Software
Organizations implementing comprehensive identity solutions transform their security posture while streamlining operations. They stop impersonation attacks that bypass traditional authentication, reduce operational friction for legitimate users, and achieve measurable fraud reduction across applications.
The question isn't whether to upgrade from device-based authentication—it's how quickly you can deploy an identity software solution that protects your enterprise while delivering exceptional user experiences.
Ready to verify people, not just devices? Request a demo to see how CLEAR1 integrates with your existing systems and delivers the multi-layered security outlined in this guide.
The workplace identity landscape has fundamentally shifted. Threat actors have abandoned traditional hacking in favor of something far more effective: impersonating legitimate users through AI-powered social engineering and synthetic identity creation.
The result? 80% of breaches now stem from system intrusion attack patterns, with 79% using malware-free tactics that perfectly mimic legitimate user behavior. The average breach has hit $4.4 million—a 10% increase year-over-year.
Most security frameworks still operate on a dangerous assumption: that possession equals identity. If someone has the password, token, or device they must be legitimate. This thinking creates vulnerabilities that today’s threat actors systematically exploit.
Instead of asking “Do you have the right credentials?” or “Is this a trusted device?” enterprises need to ask “Are you actually you?”
This guide delivers a practical framework for implementing an identity verification solution that stops impersonation attacks while streamlining legitimate access—from mapping your critical vulnerabilities to evaluating identity software vendors that offer seamless integrations with leading IAM platforms and enterprise systems, and provide robust identity verification capabilities.
Start with Your Critical Vulnerabilities
Before selecting an identity software solution, map where breaches actually happen in your organization. This exercise reveals a critical gap: most enterprises focus on technical vulnerabilities while missing the human attack vectors that sophisticated actors prefer.
Map Your High-Risk Points
These four vulnerabilities represent the most urgent threats, but comprehensive workforce identity protection extends across your entire employee lifecycle—from applicant verification and privileged access to help desk authentication and account recovery.
Account creation: A new employee is hired and needs to be onboarded into your system.
Common attack methods:
- Synthetic identity creation using stolen data
- AI-generated credentials that pass basic checks
Account recovery: An employee needs to regain access to an account or reset a password.
Common attack methods:
- Password reset exploitation through social engineering
- Security question manipulation
- Recovery process bypass through impersonation
Privileged access: An employee needs to be given permission to access sensitive or confidential information.
Common attack methods:
- Executive impersonation through social engineering attacks
- Admin rights misuse after credential theft
- Lateral movement through connected systems
Third-party access: External vendors, contractors and partners require systems access to deliver services, creating extended attack surfaces that fraudsters can exploit through social engineering. 47% of workplace breaches occurred through third-party access.
Common attack methods:
- Vendor credential exploitation
- Supply chain identity attacks
- Contractor access exploitation
Calculate the Hidden Costs of Weak Identity Verification
The numbers tell the story:
- Average cost per password reset call: $70+ per interaction
- Average number of password resets per organization annually: 923
That adds up to nearly $65,000 every year spent on password resets alone—and that doesn’t include lost productivity or security risks.
Quick assessment: If your spend on password resets and account recovery is climbing into six figures, your current identity infrastructure is failing on both security and operations efficiency.

Define Your Non-Negotiable Requirements
Resist the urge to jump into vendor demos without clear requirements. Some identity software solutions are just yesterday's authentication wrapped in modern UI. The difference between checkbox compliance and actual security lies in defining exactly what verification means in the age of AI-generated faces and synthetic identities.
Security Standards Your Solution Must Deliver
Multi-layered identity verification:
- Biometric capabilities with PAD-2 certified liveness detection: Prevents identity spoofing and AI-powered impersonation attempts by confirming physical presence and blocking deepfakes, presentation attacks, and virtual webcam injections
- Document authority validation against government-issued IDs: Prevents credential forgery and manipulation by examining security features, holograms, microprinting, and formatting details to detect counterfeit or altered documents
- Source corroboration with authoritative databases: Prevents synthetic identities and sophisticated impersonation by cross-checking personal information against both issuing authorities and trusted third-party data sources
- Device security analysis across 300+ behavioral signals: Prevents account takeovers through compromised device detection by evaluating device reputation, IP behavior, login velocity, and geolocation patterns to identify suspicious activities
- Watchlist screening for compliance requirements: Prevents high-risk transactions with prohibited parties by screening against OFAC sanctions lists, identifying politically exposed persons (PEPs), and detecting negative media associations
This multi-layered approach creates strategic redundancy where even if attackers bypass one verification method, other layers maintain protection and eliminate single points of failure that criminals systematically exploit.
Compliance certifications:
- Identity Assurance Level 2 (IAL2) for high-confidence verification
- Authentication Assurance Level 2 (AAL2) for secure access
- HIPAA compliance for healthcare environments
- SOC 2 Type II certification for enterprise deployment
Adaptive security features:
- Risk-based authentication that can be adjusted to context
- Real-time fraud detection and prevention
Beyond Implementation: Enterprise-Grade Support
CLEAR1 delivers comprehensive support that extends far beyond basic technical integration:
- Fraud Investigation: Submit verification results for triage by CLEAR's in-house security experts, including investigation protocols and escalation procedures for suspected fraud incidents
- Dedicated Technical Resources: Solutions Engineers help manage integration, configuration, and ongoing backend support, while Success Managers lead rollout planning, track performance KPIs, and drive continuous optimization
- Comprehensive Training Programs: Customized team training, live end-user support, and tailored employee communications ensure smooth adoption across your organization
This level of support transforms identity verification from a technical implementation challenge into a strategic security advantage with measurable business outcomes.
IAM Integration Requirements for Seamless Deployment
Confirm these technical capabilities before any demo:
Must-have integrations:
- Native support for leading IAM platforms like Okta, Ping Identity, and Microsoft Entra
- API-first architecture for custom workflows
- Additional enterprise integrations through orchestration partners
- Implementation timeline of days, not months
Operational requirements:
- Minimized IT oversight through turnkey integrations for integration/deployment
- Reusable identity components across applications
- Unified verification policies across multiple applications
- Scalable technology stack
User Experience Standards that Drive Adoption
Set these benchmarks for workforce acceptance:
- 95%+ completion rates for workforce use cases
- User-friendly design (as simple as the snap of a selfie)
- Reusable identity (verify once, use everywhere)
- Average verification for returning users time under 30 seconds
Build Your Evaluation Framework
Evaluate identity software through three critical lenses that determine success or failure in production environments.
Pillar 1: Technical Fit
Rate how well it integrates with your current infrastructure
Ask vendors to demonstrate:
- Integration with your existing IAM with minimal custom development
- Deployment timeline under 30 days for pilot programs
- Scalability to support your user volume, growth projections and ability to support new use cases
- API flexibility for unique workflow requirements
- Enterprise-grade security and reliability standards
Pillar 2: Security Depth and Effectiveness
Test whether it actually verifies humans, not just the device
Require vendors to prove:
- Adaptive authentication that adjusts to risk levels by use case
- Configurable assurance levels for different applications
- Fraud prevention with proven reduction rates (target: 50% minimum)
- Multi-layered approach beyond passwords and basic MFA
Pillar 3: Business Impact
Calculate ROI using this formula: (breach prevention + operational savings) / implementation cost
Demand concrete case studies like the following example.
Real-world example: Tampa General Hospital strengthened account recovery security and achieved:
- 80% of account recovery requests automated through secure self-service capabilities
- 99% faster resolution for help desk calls (MFA reset time cut from 4.5 days to 20 minutes)
- 22% reduction in all account-related support calls
- Eliminated social engineering vulnerabilities in password reset workflows
The Competitive Advantage of Modern Identity Software
Organizations implementing comprehensive identity solutions transform their security posture while streamlining operations. They stop impersonation attacks that bypass traditional authentication, reduce operational friction for legitimate users, and achieve measurable fraud reduction across applications.
The question isn't whether to upgrade from device-based authentication—it's how quickly you can deploy an identity software solution that protects your enterprise while delivering exceptional user experiences.
Ready to verify people, not just devices? Request a demo to see how CLEAR1 integrates with your existing systems and delivers the multi-layered security outlined in this guide.