The numbers are clear. 84% of security leaders reported identity-related incidents that directly impacted business operations in 2024, up from 68% in 2023. The surge in identity-related breaches contributed to U.S. cybercrime costs reaching $452.3 billion in 2024. Your board understands the threat—in 2024, their top three concerns were lost revenue, operational disruption, and reputational damage from cyber attacks.
But the risk extends far beyond traditional access points. Without comprehensive identity proofing, enterprises face equal risk of breaches from compromised identities across every touchpoint—whether it’s a fraudulent employee slipping through remote onboarding or a fake customer opening an account.
Traditional identity proofing approaches that rely on single verification methods leave critical security gaps. Today’s threat landscape demands a different approach entirely.
Why single-layer verification falls short
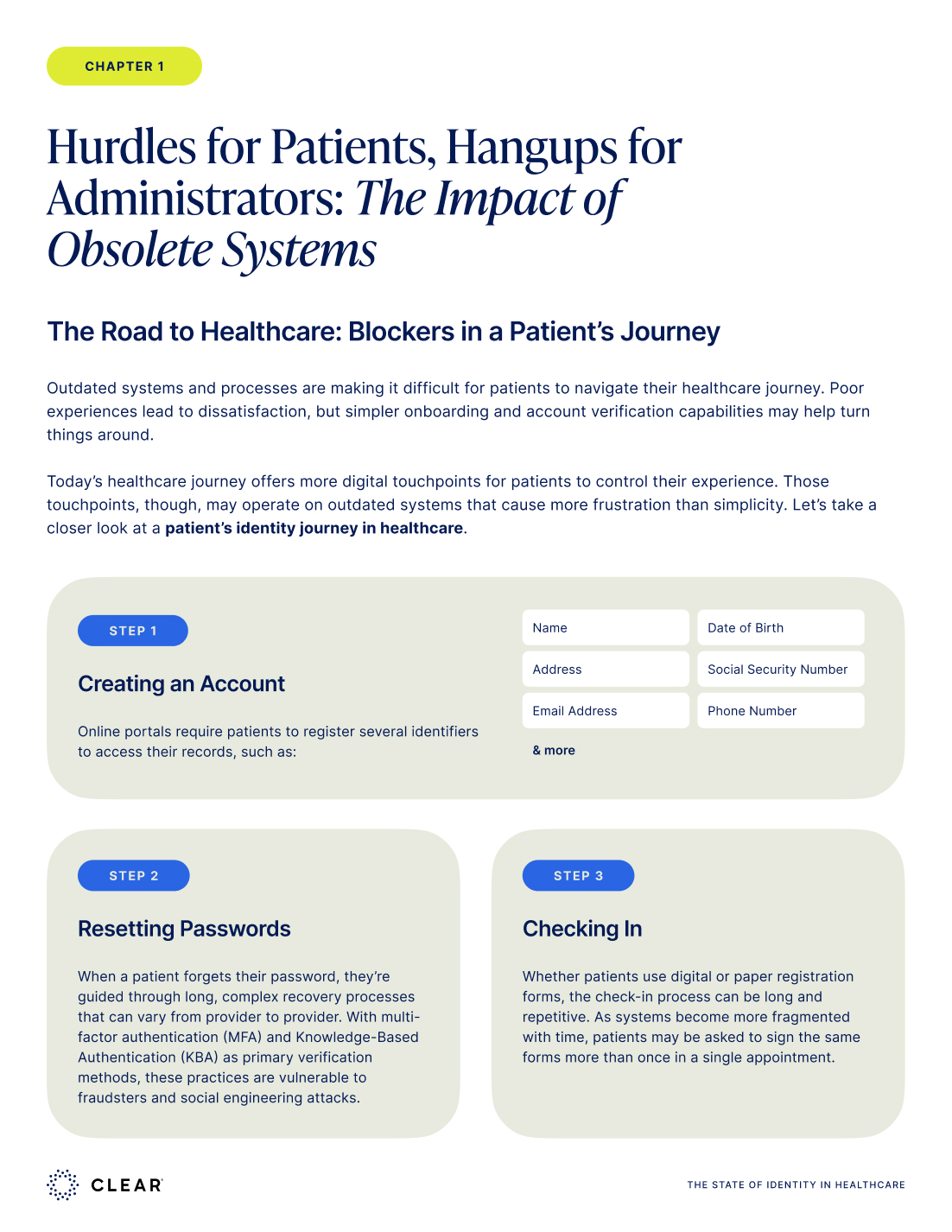
Most organizations treat identity as a simple checkpoint—a single gate to pass through. But identity isn't static. It's dynamic, contextual, and constantly evolving. Relying on one certification method leaves critical gaps that attackers exploit, creating exponential risk across the enterprise.
CLEAR1 takes a different approach. Instead of relying on one check, it analyzes thousands of signals across documents, biometrics, and verified data sources in real time. This creates three interconnected layers of protection that work together to confirm identity with unprecedented accuracy.
Layer #1: Biometric verification strengthens identity proofing security
Biometric verification—the process that uses a person’s unique physical characteristics to identify them—sounds foolproof for ID proofing. But this approach is much more vulnerable than it appears, especially as technology advances and hacker methods become increasingly sophisticated.
Why biometrics alone aren’t sufficient for identity proofing:
- Deepfakes are getting harder to detect
- Fraudsters can intercept and manipulate the data
- Stolen biometric data can be modified during transmission
Building effective ID proofing through layered biometric defense
CLEAR1’s biometric layer doesn’t work in isolation—it cross-references the selfie with the document. When a user takes a selfie, it gets compared to the photo on their government-issued ID, while liveness detection works behind the scenes to ensure it’s a real person, not a photo or video.
Fraudsters can fake one thing, but struggle to fake everything at once. Multiple verification layers—device security signals, liveness detection, and frequent selfie updates—create overlapping defenses that exponentially increase identity proofing security.
Layer #2: Document authenticity forms the identity proofing foundation
Every identity check starts with documents—driver’s licenses, passports, and government IDs. But document validation alone isn’t enough for robust ID proofing.
The problems with document-only verification:
- Forgery techniques improve constantly
- Real documents get stolen every day
- Most documents weren’t designed for digital security
- Stolen documents can appear legitimate when presented
Moving beyond single-point document verification
Document validation is a good starting point for identity proofing, but achieving identity certainty requires a more comprehensive approach. Enhanced security requires document authenticity checks that get cross-referenced with biometric signals, as well as trusted data sources, to guard against emerging threats.
Layer #3: Data cross-checking confirms legitimacy
Even if someone has a real document and their selfie matches the photo, they might still be using a stolen or synthetic identity. Source validation represents the most essential component in ensuring that credentials truly belong to the person presenting them.
Critical questions that source validation can answer in identity proofing, such as:
- Can the information on the government ID be verified against the issuing authority, such as the state DMV?
- Does the address on the government ID match the last name in one or more trusted third-party databases?
- Does the last name on the government ID match the Social Security number in one or more data sources?
- Does the phone number tie back to the user in trusted telecom or database records?
- Do any of the provided identity details match with watchlists or sanctions lists?
Why source corroboration elevates identity proofing effectiveness
Source validation detects synthetic identities that appear legitimate in isolation but fall apart under cross-reference scrutiny. Real-time validation prevents fraud using recently compromised identities by revealing inconsistencies invisible to single-system checks.
This layer transforms good ID proofing into comprehensive identity assurance by confirming that the presented information exists in official records and maintains consistency across multiple trusted sources.
Why identity proofing requires all three layers working together
Here's the crucial insight about modern identity proofing: each layer strengthens the others through interconnected verification.
- The selfie proves that the person is real, and is the same person from the document
- The document authenticity check ensures the document is real and valid
- Source corroboration confirms the identity exists in the real world with a legitimate history
The result? Fraudsters who may be able to fake one element are blocked by the interconnected layers of verification that they cannot replicate. Remove any layer, and the identity proofing system becomes vulnerable. Use all three together, and you create comprehensive protection that adapts to new threats while maintaining the user experience enterprises need.
Integrated identity protection requires unified layered defenses
When layered defenses work in concert with your existing technology stack, they establish the strong security foundation enterprises need without creating friction for legitimate users.
CLEAR1 delivers a comprehensive identity proofing solution that is 85% faster than traditional methods and reduces fraud by up to 50%.
CLEAR1’s approach to ID proofing goes beyond basic verification to provide verification checks matched to your business and regulatory requirements—including source validation and liveness detection—to deliver a multi-layered identity approach.
So whether you’re fighting fraud, securing your workforce, or elevating customer trust, CLEAR1 delivers identity assurance you and your users can count on.
The numbers are clear. 84% of security leaders reported identity-related incidents that directly impacted business operations in 2024, up from 68% in 2023. The surge in identity-related breaches contributed to U.S. cybercrime costs reaching $452.3 billion in 2024. Your board understands the threat—in 2024, their top three concerns were lost revenue, operational disruption, and reputational damage from cyber attacks.
But the risk extends far beyond traditional access points. Without comprehensive identity proofing, enterprises face equal risk of breaches from compromised identities across every touchpoint—whether it’s a fraudulent employee slipping through remote onboarding or a fake customer opening an account.
Traditional identity proofing approaches that rely on single verification methods leave critical security gaps. Today’s threat landscape demands a different approach entirely.
Why single-layer verification falls short
Most organizations treat identity as a simple checkpoint—a single gate to pass through. But identity isn't static. It's dynamic, contextual, and constantly evolving. Relying on one certification method leaves critical gaps that attackers exploit, creating exponential risk across the enterprise.
CLEAR1 takes a different approach. Instead of relying on one check, it analyzes thousands of signals across documents, biometrics, and verified data sources in real time. This creates three interconnected layers of protection that work together to confirm identity with unprecedented accuracy.
Layer #1: Biometric verification strengthens identity proofing security
Biometric verification—the process that uses a person’s unique physical characteristics to identify them—sounds foolproof for ID proofing. But this approach is much more vulnerable than it appears, especially as technology advances and hacker methods become increasingly sophisticated.
Why biometrics alone aren’t sufficient for identity proofing:
- Deepfakes are getting harder to detect
- Fraudsters can intercept and manipulate the data
- Stolen biometric data can be modified during transmission
Building effective ID proofing through layered biometric defense
CLEAR1’s biometric layer doesn’t work in isolation—it cross-references the selfie with the document. When a user takes a selfie, it gets compared to the photo on their government-issued ID, while liveness detection works behind the scenes to ensure it’s a real person, not a photo or video.
Fraudsters can fake one thing, but struggle to fake everything at once. Multiple verification layers—device security signals, liveness detection, and frequent selfie updates—create overlapping defenses that exponentially increase identity proofing security.
Layer #2: Document authenticity forms the identity proofing foundation
Every identity check starts with documents—driver’s licenses, passports, and government IDs. But document validation alone isn’t enough for robust ID proofing.
The problems with document-only verification:
- Forgery techniques improve constantly
- Real documents get stolen every day
- Most documents weren’t designed for digital security
- Stolen documents can appear legitimate when presented
Moving beyond single-point document verification
Document validation is a good starting point for identity proofing, but achieving identity certainty requires a more comprehensive approach. Enhanced security requires document authenticity checks that get cross-referenced with biometric signals, as well as trusted data sources, to guard against emerging threats.
Layer #3: Data cross-checking confirms legitimacy
Even if someone has a real document and their selfie matches the photo, they might still be using a stolen or synthetic identity. Source validation represents the most essential component in ensuring that credentials truly belong to the person presenting them.
Critical questions that source validation can answer in identity proofing, such as:
- Can the information on the government ID be verified against the issuing authority, such as the state DMV?
- Does the address on the government ID match the last name in one or more trusted third-party databases?
- Does the last name on the government ID match the Social Security number in one or more data sources?
- Does the phone number tie back to the user in trusted telecom or database records?
- Do any of the provided identity details match with watchlists or sanctions lists?
Why source corroboration elevates identity proofing effectiveness
Source validation detects synthetic identities that appear legitimate in isolation but fall apart under cross-reference scrutiny. Real-time validation prevents fraud using recently compromised identities by revealing inconsistencies invisible to single-system checks.
This layer transforms good ID proofing into comprehensive identity assurance by confirming that the presented information exists in official records and maintains consistency across multiple trusted sources.
Why identity proofing requires all three layers working together
Here's the crucial insight about modern identity proofing: each layer strengthens the others through interconnected verification.
- The selfie proves that the person is real, and is the same person from the document
- The document authenticity check ensures the document is real and valid
- Source corroboration confirms the identity exists in the real world with a legitimate history
The result? Fraudsters who may be able to fake one element are blocked by the interconnected layers of verification that they cannot replicate. Remove any layer, and the identity proofing system becomes vulnerable. Use all three together, and you create comprehensive protection that adapts to new threats while maintaining the user experience enterprises need.
Integrated identity protection requires unified layered defenses
When layered defenses work in concert with your existing technology stack, they establish the strong security foundation enterprises need without creating friction for legitimate users.
CLEAR1 delivers a comprehensive identity proofing solution that is 85% faster than traditional methods and reduces fraud by up to 50%.
CLEAR1’s approach to ID proofing goes beyond basic verification to provide verification checks matched to your business and regulatory requirements—including source validation and liveness detection—to deliver a multi-layered identity approach.
So whether you’re fighting fraud, securing your workforce, or elevating customer trust, CLEAR1 delivers identity assurance you and your users can count on.